The Health Insurance Portability and Accountability Act, or HIPAA, sets the standard for safeguarding for patient data safety and security in the healthcare industry.
It regulates how healthcare organizations use, store, and share protected health information (PHI).
In other words, you must be familiar with HIPAA.
However, knowing exactly what to do to ensure your practice is HIPAA-compliant is a whole other ballgame.
Considering how complex HIPAA regulations are, we’ve prepared a HIPAA compliance checklist that will guide you through the key steps to ensure your practice meets HIPAA standards.
So, whether you’re setting up a new clinic or reviewing your current protocols, we’ve got you covered.
Who needs to be HIPAA compliant?
First things first – let’s explore who’s held accountable before the federal law.
It’s not only healthcare practices that have to make sure they’re HIPAA compliant. There are three main covered entities to which HIPAA applies.
- Covered Entities which are defined in the HIPAA rules as:
- Healthcare providers include healthcare organizations and individuals who directly handle patient health information (PHI) or electronic protected health information (e-PHI), like doctors, GPs, hospitals, clinics, medical spas, etc).
- Health plans include insurance companies, HMOs, government programs like Medicare and Medicaid, employer-sponsored health plans and Medicare prescription drug card sponsors.
- Healthcare clearinghouses include organizations that process health information for billing or other purposes and convert non-standard electronic data formats into standardized formats for easier data exchange between providers, patients and other entities.
Two other main entities that need to follow HIPAA rules are:
- Business Associates (BAs) are individuals or companies that provide services to covered entities, like third-party billing, IT services, medical transcriptions, and cloud storage. They must sign a Business Associate Agreement (BAA) that states they need to protect PHI.
- Subcontractors of BAs are third-party providers hired by BAs to handle PHI, such as a software company that stores or processes PHI.
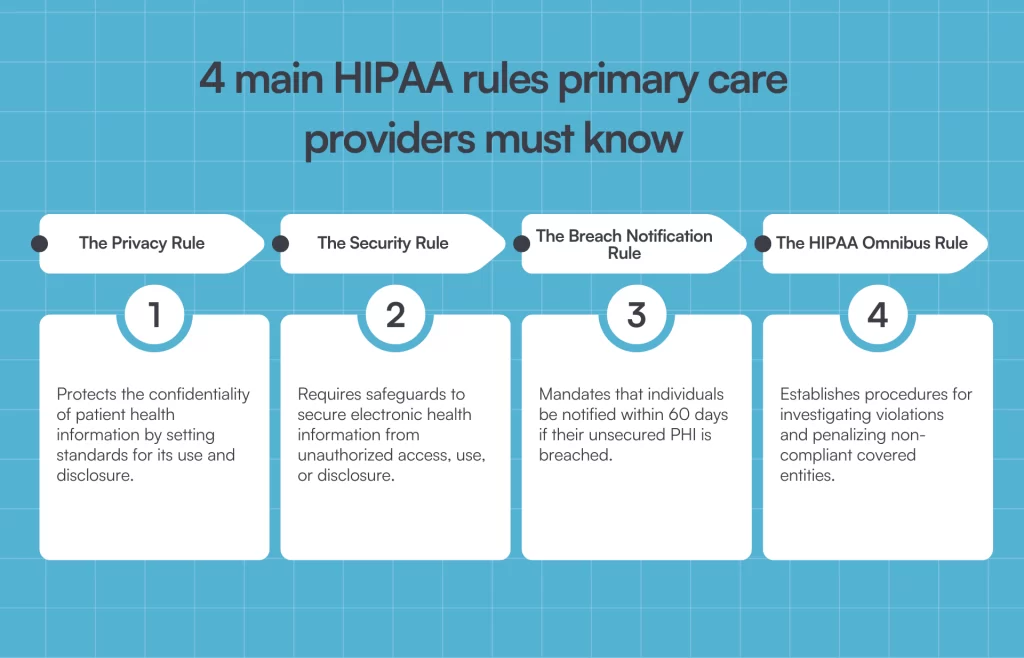
What are the 4 main HIPAA rules that primary care providers must know?
These are the 4 HIPAA rules that define HIPAA compliance requirements:
- The HIPAA Privacy Rule: Limits who can access and share PHI and protects patients’ rights over their health data.
- The HIPAA Security Rule: Standards for safeguarding e-PHI with administrative, physical, and technical safeguards.
- The HIPAA Breach Notification Rule: Requirement for reporting security incidents that can compromise patient data security to authorities and patients.
- The HIPAA Omnibus Rule: The latest HIPAA update, expanding and clarifying HIPAA protections, particularly for BAs and subcontractors.
Below, we’ll stick to the Security Rule and the four administrative, physical, and technical safeguards that primary care practices implement to protect e-PHI.
Ensure confidentiality, integrity, and availability of e-PHI
To comply with HIPAA’s Security Rule, primary care providers must safeguard all e-PHI to maintain its confidentiality, integrity, and availability across all platforms.
- Confidentiality means that e-PHI should only be accessible to authorized individuals. Only staff members with permission can view or modify patient data.
- Integrity involves ensuring that e-PHI is not altered or tampered with in any unauthorized manner.
- Availability indicates that authorized users can easily and securely access e-PHI when they need to treat patients.
Identify and protect against security threats
It’s really important to be proactive in identifying and mitigating potential risks for e-PHI so you’re not caught off guard.
Perform regular risk assessments to identify vulnerabilities in your systems and processes, such as outdated software, weak passwords, practitioners sending patient information to the wrong recipient, and employees accessing e-PHI on personal devices.
Protect against unauthorized uses or disclosures
You can’t control if a data breach happens, but you can implement security measures to prevent unauthorized access, use, or sharing of electronic protected health information.
Restrict access to e-PHI based on job roles so only authorized personnel can view or modify patient information.
Another effective measure is to set up two-factor or multi-factor authentication (MFA) for accessing e-PHI systems.
We’ll cover more technical, administrative and physical safeguards below.
Ensure workforce compliance
Since your employees handle sensitive information, you need to train them on the importance of HIPAA regulations, the security of PHI, how to identify phishing scams, and how to handle data securely.
Provide mandatory and ongoing HIPAA training for all employees so they understand the importance of protecting patient information.
Cover key topics like data security, how to safely handle e-PHI, how to handle patient requests, what information they can’t and mustn’t share on social media, etc.
What are the penalties for non-compliance with HIPAA?
If you fail to protect patient information, even unintentionally, the Office for Civil Rights and the Department of Health and Human Services (HHS), the two organizations that enforce HIPAA, will open an investigation.
If you’re found to have broken the rules, you’ll be fined for HIPAA non-compliance.
These are the four tiers of penalties for HIPAA non-compliance:
- Tier 1: Unknowing violation corrected within 30 days. This penalty is given when the covered entities and business associates were unaware of the violation and could not have reasonably avoided it. Fines range from $100 to $50,000 per violation.
- Tier 2: Unknowing violation not corrected within 30 days or reasonable time. This applies when the covered entity or business associate was unaware of the violation but didn’t take action within 30 days. It leads to stricter penalties from $1,000 to $50,000 per violation.
- Tier 3: Willful neglect corrected within 30 days. This penalty is imposed if the covered entity was aware of the violation but didn’t prevent it. The fines range from $10,000 to $50,000 per violation.
- Tier 4: Willful neglect not corrected within 30 days. This is when the violation was intentional and the covered entity failed to correct it within 30 days. The fine is $50,000 per violation, with an annual maximum of $1.5 million for repeated violations.
In some cases, a HIPAA violation can be considered a criminal offense and can result in prison time of up to ten years if it involves the intentional misuse or theft of PHI and leads to personal gain and malicious harm.
HIPAA compliance checklist for primary care providers: 10 steps
We’ve compiled a 10-step compliance checklist to help you make your practice compliant with HIPAA regulations and protect sensitive health information.
1. Risk analysis and management
Risk analysis helps you find weak spots in how you handle electronic PHI and take steps to reduce the possibility of data breaches and HIPAA violations.
The Department of Health and Human Services lists the following key activities for security risk assessment:
- Evaluate the likelihood and impact of potential risks to e-PHI, such as outdated systems, mobile devices, or third-party services.
- Implement appropriate security measures to address the risks identified in the risk analysis, like end-to-end data encryption, password policies, or access control.
- Document the chosen security measures and, where required, the rationale for adopting those measures.
- Maintain continuous, reasonable, and appropriate security protections.
2. Administrative actions and policies
Administrative safeguards focus on internal processes and policies necessary to protect patient information and how staff members access and handle e-PHI. They cover the following actions:
- Security management process for identifying potential risks and vulnerabilities.
- Security personnel: Assign a security and privacy officer who will be in charge of security policies and procedures.
- Information access management: Give employees access to e-PHI based on their role within the organization. A system like Pabau can help you with role-based access control.
- Workforce training and management: Everyone who handles sensitive patient information must undergo training on key HIPAA requirements.
Evaluation: Periodically assess your security policies and procedures and update them to align with the HIPAA Security Rule.
3. Physical safeguards
Physical security measures are essential for protecting the facilities and equipment that store or process PHI.
You need to implement facility access controls that limit who can enter areas where PHI is stored or processed, such as keycard or biometric entry systems, security cameras, visitor management protocols, and so on.
Additionally, workstations and devices that access or store PHI should be physically secured to prevent unauthorized use. This includes:
- Placing devices in secure areas
- Locking up computers and portable devices when not in use
- Requiring passwords or biometric verification to log in
4. Technical safeguards
Technical safeguards are crucial for preventing unauthorized access, modifying, and sharing e-PHI and ensuring that all activities involving e-PHI are secure and traceable. The technical security standards cover:
- Access controls: Each user should have a unique username and password, ensure automatic log-offs on the system after a period of inactivity and role-based access control.
- Audit controls: Set up audit logs to track access and actions involving e-PHI, perform real-time monitoring, and alert employees of suspicious activity.
- Integrity controls: Implement systems that detect any unauthorized alteration or tampering with e-PHI.
- Transmission security: Involves preventing unauthorized access to e-PHI that is transmitted over an electronic network through secure communication channels and VPNs for remote access to e-PHI
5. Privacy rule compliance
The HIPAA Privacy Rule mandates that PHI and ePHI can be used or disclosed only for treatment, payment, or healthcare operations.
You can’t share it for purposes not related to healthcare (e.g., marketing, research), and you should get signed consent from the patient before sharing PHI in these cases.
Patients also have the right to access and request copies of their medical records. As a provider, you have up to 30 days to provide access.

6. Breach notification rule compliance
The Breach Notification Rule requires you to take concrete actions in case a data breach happens that puts patients’ data at risk.
If an incident occurs, you must report it to the Office for Civil Rights (OCR) and inform affected patients within 60 days. You also need to document each HIPAA breach, make efforts to mitigate the harmful effects of the breach, and take steps to improve your patient data protection and privacy practices.
7. Regular audits and reviews
HIPAA compliance is not a one-time task. Conducting regular audits and reviews helps identify potential gaps in policies and address risks before they lead to full-blown violations.
Audits include checking:
- Who has access to systems that store e-PHI
- Audit logs and system activity reports that can reveal suspicious activity or unauthorized access
- If your HIPAA policies and procedures are updated to cover new technologies and situations
- If your incident response plan reflects current procedures for handling breaches or cybersecurity incidents
8. Documentation and record-keeping
All your HIPAA compliance efforts need receipts. Properly documenting HIPAA-related policies, procedures, and incidents means you can show proof of compliance during audits, quickly respond to security issues, and maintain accountability in your practice.
Also, HIPAA mandates that healthcare providers keep specific documentation for a minimum of six years. These records must be accessible and up-to-date and reflect your current compliance practices.
9. Contingency planning
Having a contingency plan helps you make sure protected health information is secure and accessible during emergencies, cyber-attacks, natural disasters, or technical failures.
This means:
- Doing regular backups of all critical data, including patient records, billing information, and scheduling systems.
- Having a documented, detailed plan with the steps required to restore access to critical systems and ePHI after a disaster.
- Assigning specific roles and responsibilities for staff members. For example, IT personnel are responsible for restoring systems and administrative staff for managing communications.
- Creating an emergency mode operation plan with protocols on how to access PHI and provide care until systems are temporarily down.
10. Employee termination procedures
When an employee leaves your practice, you need to make sure they can no longer access your systems or data in order to prevent unauthorized access to ePHI. Having a repeatable process to do this is crucial.
After their termination, immediately deactivate their user accounts and retrieve any keys or access badges they used to access your practice, as well as any company laptops, tablets or smartphones.
The importance of HIPAA-compliant practice management software
A critical part of being HIPAA-compliant is having practice management software that can support your compliance efforts — to safeguard patient information, streamline daily operations, and ensure legal compliance.
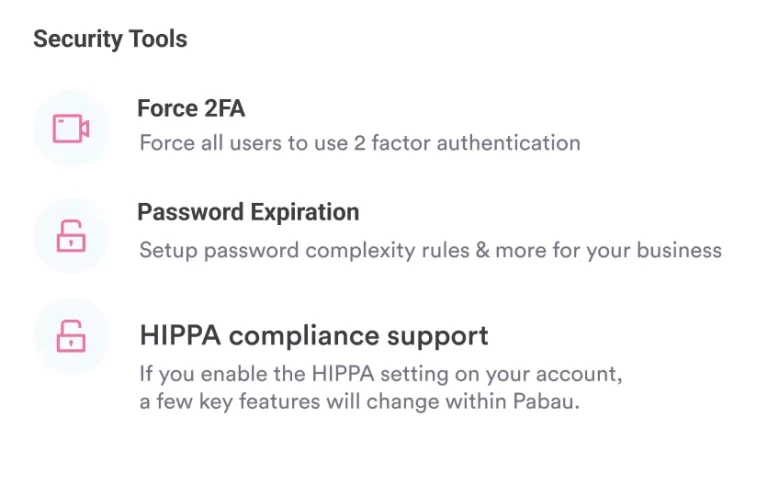
Pabau is an all-in-one practice management software with advanced security features that give you a much-needed boost in your compliance journey:
- Data encryption
- Secure hosting
- Role-based access control and user authentication
- 2-factor authentication
- Audit logs and trails
- Regular data backups and disaster recovery
Remember, we provide you with the tools to support your HIPAA compliance efforts. But it’s not a magic wand. Only using Pabau doesn’t guarantee compliance – it’s still up to you to take the steps toward being compliant.
Maintain HIPAA compliance seamlessly with Pabau
HIPAA compliance isn’t exactly simple, but following the structured checklist will get you on the right path to making your practice fully HIPAA-compliant.
However, it’s impossible to do it single-handedly. Pabau gives you the right tools to support HIPAA compliance in an efficient and secure way.
Whether you’re opening a new primary care practice or want to ensure full compliance with HIPAA regulations, book a demo and see how Pabau can help you on your journey.




